What you need to know about the Cybersecurity Maturity Model Certification (CMMC)
Jul 20, 2020 - Robert Thurston

Many businesses provide services to the US federal government, and as they know it is not always an easy process. Adherence to the Federal Acquisition Regulations (FAR) and its various addendums such as the Defense Federal Acquisition Regulation Supplement (DFARS) can at times be extremely challenging.
Recently, in light of the many cybersecurity threats faced by our nation, DFARS clause 252.204-7008 titled Compliance with Safeguarding Covered Defense Information Controls was instituted, which requires both prime contractors and subcontractors to adhere to a very strenuous set of cyber security controls and practices known as NIST Special Publication 800-171.
NIST SP 800-171 Vital Statistics
- 14 families or categories of security requirements
- 110 individual security program requirements, all of which must be met
- 101 pages in the standard itself as of revision 2 in February 2020
- 82 pages in the NIST SP 800-171A providing requirements for how to assess security requirements and performance of security programs
Luckily for some organizations, compliance with these requirements is largely a self-attestation process. However, some organizations, when audited by their federal contracting partners were found to be in violation and were subject to penalties. Further, making false or misleading representations to the federal government can be a violation of the False Claims Act and result in significant penalties.
Unfortunately, most organizations are not well prepared to stand up and implement a fully compliant cyber security program and those that are may underestimate the cost and complexity of doing so. If your organization is considering moving towards a federally compliant security program first, you need to ask yourself a few important questions:
Will the new business and value I derive from providing service to the federal government cover my costs of compliance?
Building out a fully compliant cybersecurity program can be very costly to an organization. Even more sophisticated medium sized businesses may need to hire additional cybersecurity and compliance experts to champion the program.
Consider carefully how you structure your federal contracts and proposals to make sure you cover all your costs appropriately.
Do I have the required expertise in my organization to faithfully execute on the requirements for cyber security?
Even if your organization is willing to hire on an expert in this field, they can be hard to find. Many veteran cybersecurity managers and analysts command excellent salaries and benefits in a tightly competitive market. Moreover, when the potential penalties for a breach or misrepresentation are so high, the risk of hiring a single individual to manage your cybersecurity program can multiply quickly.
How quickly do I need to become compliant?
If you take on a contract subject to DFARS requirements, you have 30 days from the commencement of the contract to be fully compliant or to provide notice to the federal government that you are not compliant.
If you are not compliant, you can expect that they will ask you to submit a Systems Security Plan and Controlled Unclassified Information Plan of Action, so make sure those documents are ready!
Once you submit your Plan of Action, you’ve made a strong commitment to your federal partner to perform, so keep in mind that you have to be dilligent in execution. Many organizations are seeing between 12 and 18 months of continual effort to fully complete their compliance projects.
Am I willing to sustain this effort?
Cyber security is not a static field, the threat landscape is continually changing. Reflecting this fact, you will find that cyber security standards continue to evolve and your technology systems will require upkeep to stay effective.
While it may be tempting, resist the urge to consider cyber security compliance a “one and done” problem. You need to operationalize these practices into our organization for the long term in order to be successful and safeguard the data of your federal clients.
Introducing the Cybersecurity Maturity Model Certification (CMMC)
Just as many organizations were getting compliant with NIST SP 800-171, the federal government upped the ante to play or “moved the cheese”, if you prefer. After seeing a lackluster response with the original program, largely based on self-attestation, the government has implemented the new Cybersecurity Maturity Model Certification. You can expect to see forward moving procurements and requests for proposal (RFP) issued by federal agencies to include these requirements.
How much more is there to do?
The CMMC introduces 5 levels of compliance certification, each with differing levels of sophistication and complexity.
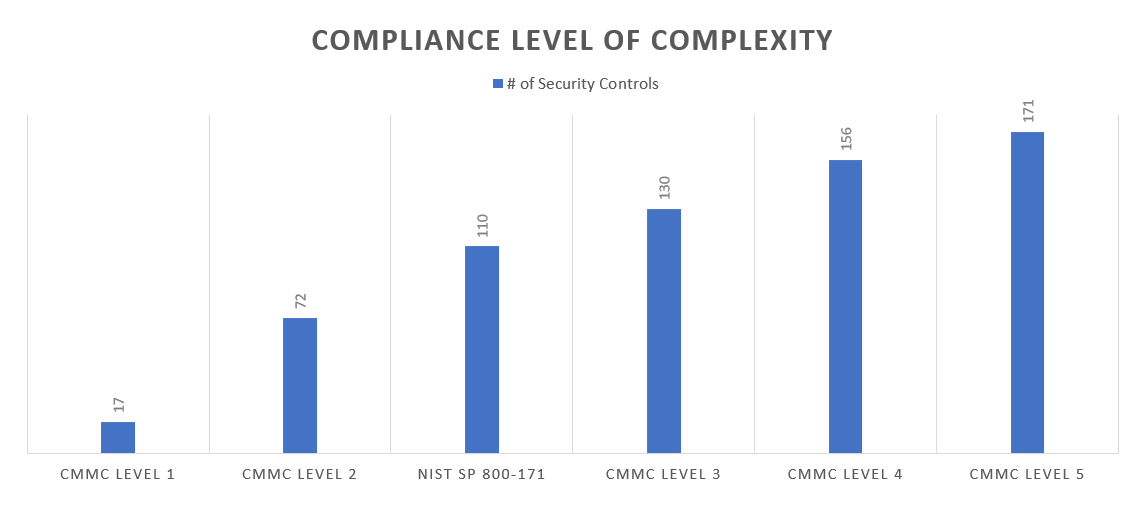
Unfortunately, the level of effort to move between CMMC certification levels is not strictly a linear relationship with the total number of controls, as it is intended that the overall sophistication of a security program increases significantly as your organization achieves a higher level of compliance certification.
Who provides the certification?
Currently, you are not able to actually receive a CMMC certification, as the CMMC Accreditation Body (CMMC-AB) has not yet certified 3rd party assessor organizations (C3PAO). It is expected that formal and commercially available certifications will begin in the later half of 2021, which will involve a full third party assessment of your information security controls.
In the meantime, the CMMC-AB has started the process of qualifying Registered Provider Organizations (RPO) who have background and expertise in helping organizations build their security programs toward a goal of CMMC compliance.
Where do I start?
AlasConnect is a full scale technology service provider helping our clients with both NIST SP 800-171 and CMMC compliance solutions. Contact us if you’d like to start working towards a formal certification or even just a baseline health check of your existing information security practices.